
UK security chief warns major cyberattack is a matter of ‘when, not if’
Ciaran Martin said the country is lucky to have avoided a category one threat, which could cripple infrastructure, the financial markets or interfere in elections
The head of the UK’s National Cyber Security Centre has warned that a major cyberattack on the UK is a matter of “when, not if”, raising the prospect of devastating disruption to British elections and critical infrastructure.
In remarks underlining newly released figures showing the number of cyberattacks on the UK in the last 15 months, Ciaran Martin said the UK had been fortunate to avoid a so-called category one (C1) attack, broadly defined as an attack that might cripple infrastructure such as energy supplies and the financial services sector.
The US, France and other parts of Europe have already faced such attacks.
Interference in elections would also constitute a C1 attack, as would a deliberately provocative move by a hostile state.
During an hour-long interview with The Guardian, Martin said he anticipated such an attack in the next two years.
“I think it is a matter of when, not if and we will be fortunate to come to the end of the decade without having to trigger a category one attack,” he said.
He admitted total protection was impossible. “Some attacks will get through. What you need to do [at that point] is cauterise the damage,” he said.
Martin was speaking last week before a speech on Monday by the chief of the general staff, Sir Nick Carter, in which he highlighted the growing threat posed from cyberattacks, in particular from Russia, both on the battlefield and on civilian services.
The NCSC, which is the front window for the government surveillance agency GCHQ, has been gradually building defences and is due to publish soon a 60-plus page dossier outlining what has worked and what has not since it opened for operations in October 2016.
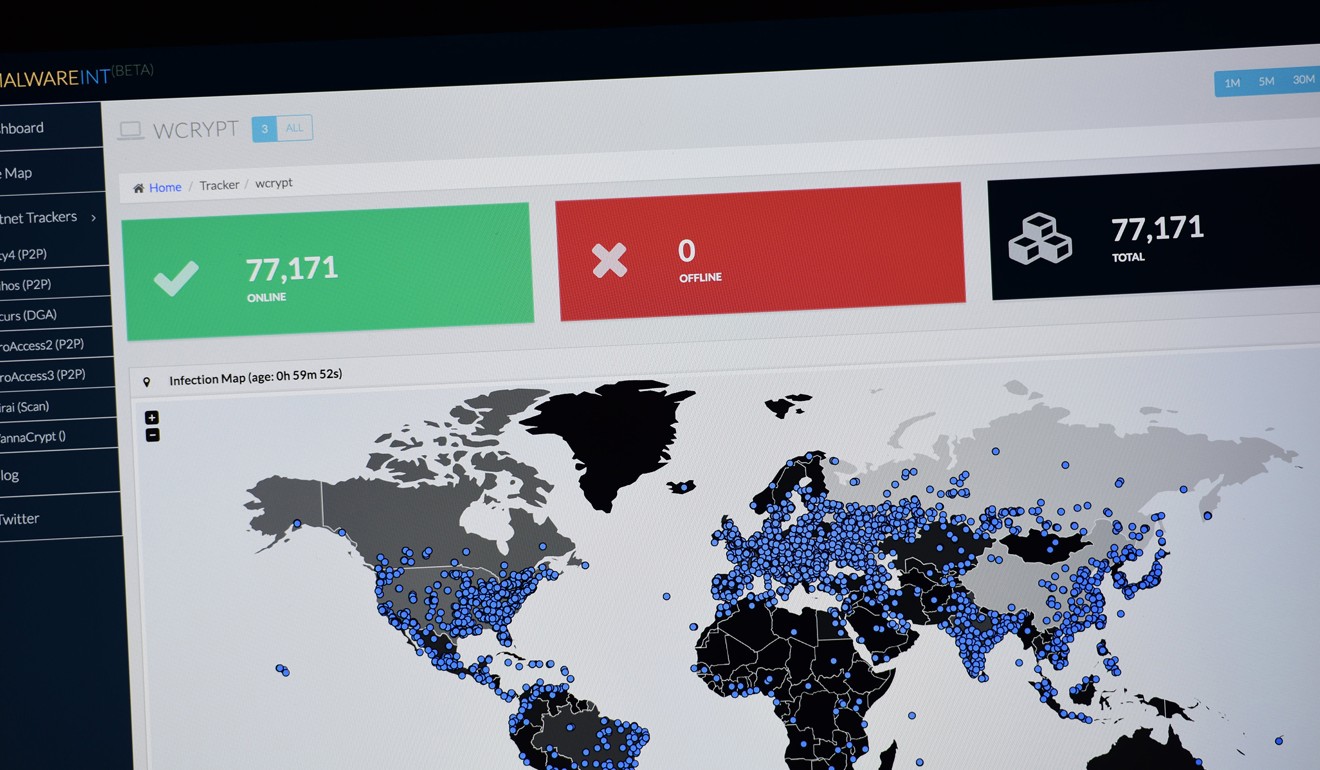
The most serious cyberattack on the UK so far was the WannaCry ransomware attack in May last year that disrupted hospitals. In spite of its impact, the attack was classified as only C2 rather than C1, partly because there was no risk to life.
Figures for cyberattacks since the NCSC opened through to December last year underline the pressure building on the UK from hackers. The NCSC recorded 34 C2 attacks, with WannaCry the most disruptive of these, and 762 slightly less serious C3 ones.
Watch: US warns of new ransomware worm
“Most comparable western countries have experienced what we would consider a category one attack so we have been fortunate in avoiding that to date,” said Martin, who is chief executive officer at the NCSC and former director general for cyber-security at GCHQ.
Among serious breaches elsewhere are the hacking of the US Democratic Party in the run-up to the 2016 White House election and an attack on a French television station in 2015, both blamed on Russia.
The NCSC, as part of its preparations against similar attacks, has been advising key departments and companies on vulnerabilities while intelligence agencies monitor potential hackers. There is also an emergency response team on constant standby.
What we have seen from Russia thus far against the UK is a series of intrusions for espionage
Martin said one of the biggest lessons from 2017 was to fear reckless as much as controlled attacks. He considered WannaCry, which was blamed on North Korea, as an example of an attack in which the perpetrator loses control.
“What we have seen over the past year or so is a shift in North Korean attack motivation from what you might call statecraft – disrupting infrastructure – through to trying to get money through attacks on banks but also the deployment of ransomware, albeit in a way that didn’t pan out in the way the attackers wanted to.”
As well as North Korea, intrusions have been blamed on Russia, China and Iran. Some of these, Martin said, were espionage-based, scouting out vulnerabilities in infrastructure for potential future disruption. Although the UK signed a treaty with China in 2015 not to engage in cyberattacks for commercial gain, espionage was left out of the treaty.
“What we have seen from Russia thus far against the UK is a series of intrusions for espionage and possible pre-positioning into key sectors but in a more controlled form of attack from others,” he said.
The UK has publicly acknowledged its growing cyber-offensive capabilities. Martin, while saying it was a matter not for him but GCHQ and the Ministry of Defence, said: “Offensive cyber will be an increasing part of the UK’s security toolkit.”
But he cautioned against assuming a cyberattack from another state would trigger a retaliatory cyberattack, saying there were a range of responses from diplomatic pressure through to sanctions and indictments.
The Trump administration has raised the prospect of using nuclear weapons in response to a major cyberattack.
Martin said he had not seen any successful attempt to interfere in the UK democratic process. The political parties had originally been suspicious about taking advice from an organisation linked to the intelligence agencies when the NCSC first opened.
When Theresa May called the UK general election in April, much of that reticence disappeared, Martin said, possibly because of the experience in the US and France.
“The main parties in the House of Commons did ask for and did receive guidance on the sort of threats they were likely to face and we worked with each of them,” Martin said.
Cyberattacks appear to have made electronic voting less likely in the future. “With the current state of high alert around elections, I think it make sense that there are not any current plans to move to electronic voting,” Martin said.
Electoral security is one of the areas in which the NCSC is working closely with European Union counterparts. In spite of reports of concerns over security cooperation post-Brexit, Martin insisted: “There is significant momentum in Europe to get the European cybersecurity across the whole continent on a stronger footing and that is great.”
Among challenges facing Martin, he identified encouraging more girls to consider engineering and computing as a career. Of the NCSC’s 700-strong workforce, only 32% are female, though half of the roughly 20 senior management posts are held by women.

